You’ve built an incredible web application. It’s sleek, functional, and ready to make waves online. But before launching it, there’s one crucial question to ask: is it secure?
That’s where security testing steps in as your digital safeguard. It identifies weak points in your app that hackers could exploit to steal data or cause disruptions. Just like you wouldn’t build a house without checking for weak spots, your web app needs the same level of care to stand strong against potential threats. Security testing in software testing ensures your app or system is prepared to handle any attacks it might face.
As technology grows, so does the risk of cybercrime. Cyberattacks are happening more often and becoming more complex and dangerous. Cybercrime is expected to cause damages of $9.5 trillion USD worldwide in 2024. These threats expose sensitive information, disrupt business operations, and reduce user trust.
Every organization needs to have a clear plan to defend against cyberattacks. Security testing in software testing helps to tackle these issues by identifying loopholes and weaknesses in the system that could lead to data loss or damage to the organization. Security testing can identify potential security risks and address vulnerabilities early, helping to protect applications from cybercriminals and prevent possible exploits.
In this blog, we will explore the fundamentals of security testing in software testing, discuss the various types, techniques and tools used to strengthen application security, and examine the benefits and limitations of security testing.
What is Security Testing in Software Testing?
Security testing in software testing is the process of finding vulnerabilities and weaknesses in software to prevent unauthorized access, data breaches, and potential threats. It identifies susceptible passwords, unpatched software, or misconfigured systems and stops hackers from causing harm to the system. By testing for security flaws, it protects both the software and the users’ data.
With the rise in cyberattacks, security testing evaluates the security of a system and helps organizations prepare against potential security incidents. Combining various testing techniques to test the security of data and functionalities helps build trust with users by keeping their information safe.
Principles of Security Testing in Software
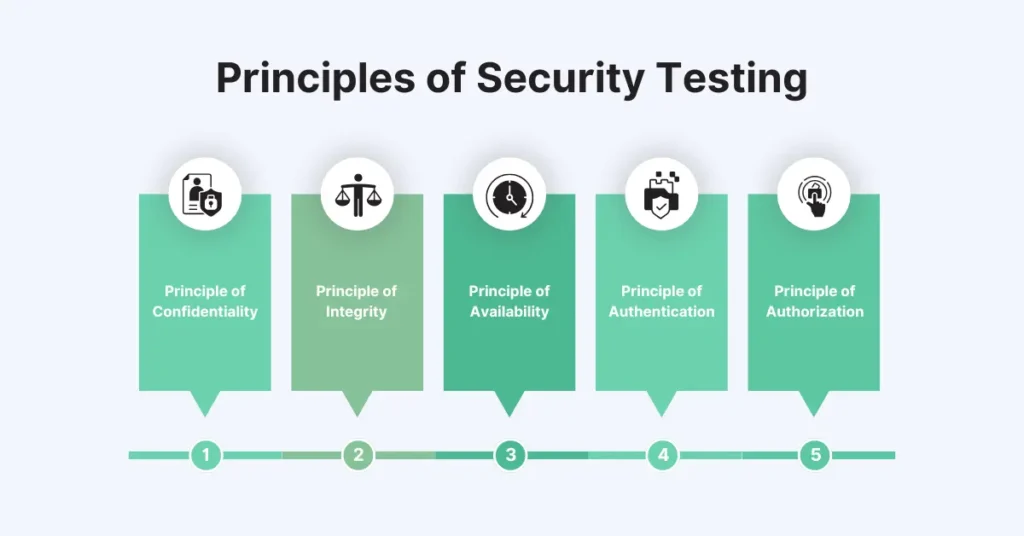 Security testing in software testing is based on five key principles, each of which addresses a critical aspect of keeping software and systems secure:
Security testing in software testing is based on five key principles, each of which addresses a critical aspect of keeping software and systems secure:
• Principle of Confidentiality: This principle ensures that sensitive information is only accessible to authorized users. Security testing in software testing helps confirm that data, such as personal or financial information, is protected against information leakage to unwanted recipients.
• Principle of Integrity: Integrity ensures that data remains accurate and unmodified. Software Security testing checks that data cannot be tampered with or corrupted, maintaining its accuracy and reliability.
• Principle of Availability: Availability ensures that the system and its data are accessible to authorized users whenever needed. Security testing in software testing ensures that there is a data availability plan to recover from attacks that may attempt to disrupt service.
• Principle of Authentication: Authentication is a set of security measures to verify the identity of users trying to access the system. Software security testing ensures that only legitimate users can gain access to information by confirming the effectiveness of login procedures such as passwords, biometrics, or multi-factor authentication.
• Principle of Authorization: Authorization is the process of giving users permission to access specific resources or perform certain actions. Security testing in software testing confirms that access control measures are in place, ensuring that only users can perform tasks they are authorized to do.
Security Test Cases and Scenarios
Security test cases in software testing focus on assessing different aspects of an application to ensure that it is protected against possible threats. When designing security test cases, it is important to assess the impact and likelihood of each vulnerability and focus testing efforts based on the level of risk. Here are a few critical areas to be considered:
• Authentication: Test cases for authentication focus on verifying that only authorized users can access the system. Common scenarios include testing login mechanisms, password strength requirements, multi-factor authentication, and protections against brute-force attacks. For instance, testing whether the system locks out users after several failed login attempts helps ensure proper authentication security.
• Input Validation: Input validation test cases ensure that user data is properly sanitized to prevent harmful inputs from affecting the application. These scenarios typically cover issues such as SQL injection, cross-site scripting (XSS), and buffer overflows. For example, testing how the system handles unexpected or malicious inputs (such as special characters in a text field) helps prevent security vulnerabilities.
• Application and Business Logic: Test cases in this area ensure the application’s core logic is secure and works as expected. This includes checking access control, enforcing business rules within a specific application, and preventing unauthorized actions such as elevating user privileges. For example, tests may check if a regular user can access admin features or bypass workflow limits.
By focusing on these elements, security testing in software testing can identify and fix vulnerabilities that could threaten the safety and integrity of the system.
Types of Security Testing in Software Testing
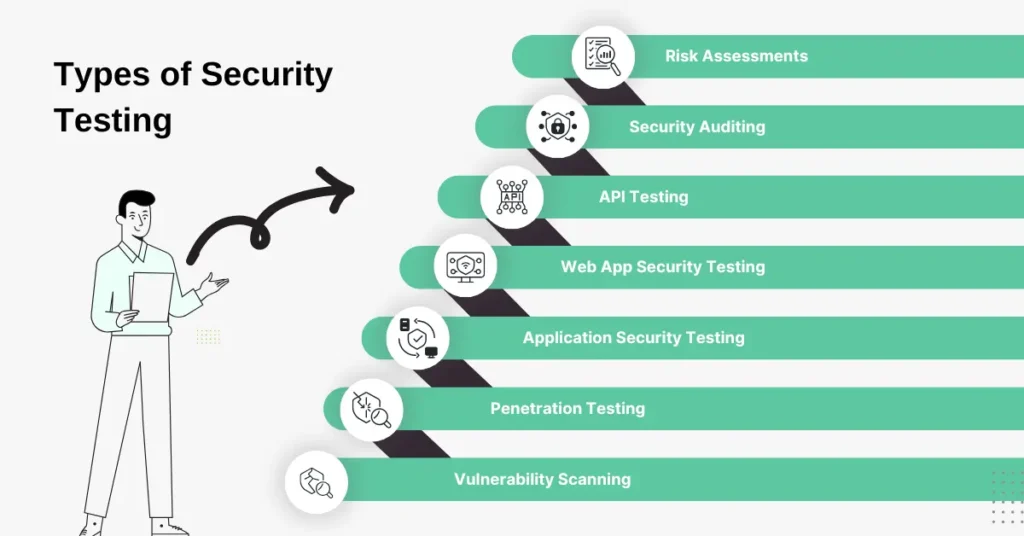 Security testing in software testing encompasses various methods to ensure that applications and systems are secure from possible threats. Below are the key security testing types as per Open Source Security Testing methodology manual:
Security testing in software testing encompasses various methods to ensure that applications and systems are secure from possible threats. Below are the key security testing types as per Open Source Security Testing methodology manual:
- Vulnerability Scanning: This automated process identifies known vulnerabilities within a system. Tools scan for outdated software, misconfigurations, or missing security patches, helping to pinpoint weaknesses that attackers could exploit.
- Penetration Testing: Penetration testing simulates malicious attacks to identify if the system or network can be penetrated. Ethical hackers attempt to break into systems to expose flaws including configuration, poor architecture, vulnerabilities, and weak processes before malicious actors can do so.
- Application Security Testing: This type of security testing in software testing focuses on the overall security of a software application. It ensures that all security controls, such as encryption and authentication mechanisms, are working as intended to protect the application from threats.
- Web App Security Testing: Web applications are often prime targets for cyberattacks. Web app security testing evaluates the security of a web-based application by looking at and fixing vulnerabilities such as SQL injection, cross-site scripting (XSS), and session management flaws.
- API Testing: Application Programming Interfaces (APIs) provide a set of tools for building applications and enable communication and data exchange from one software system to another. API testing checks that these interfaces are secure, ensuring they handle requests and responses safely and protect sensitive data.
- Security Auditing: A security audit is a systematic review of the security measures of a system to verify its compliance with industry standards and policies. This process assesses the current security posture and identifies areas for improvement.
- Risk Assessments: Security risk assessment involves identifying, evaluating, and ranking risks based on their potential impact. It helps organizations understand how likely and severe threats are, and develop plans to reduce them. It prevents application security defects and vulnerabilities.
- Security Posture Assessments: An overall review of an organization’s complete security readiness, this assessment evaluates whether security measures are properly implemented and effective at protecting against threats. It includes evaluating both technical and non-technical controls.
Different Approaches to Security Testing
Security testing in software testing can be performed using several approaches, each providing a different perspective on identifying vulnerabilities:
• Black Box Testing: In this approach, the tester has no prior knowledge of the internal workings of the application. They simulate an external attacker’s perspective, probing for vulnerabilities solely based on what they can observe or access from the outside. Black box testing helps identify flaws that external hackers may exploit, without knowing the system’s internal logic or architecture.
• Grey Box Testing: Grey box testing combines elements of both black box and white box approaches. It is a software testing method where the tester, with limited knowledge of the system, tests software applications, typically with access to certain internal details such as code structure or documentation.
• Tiger Box Testing: Tiger box testing is a highly specialized form of security testing that focuses on a particular system or component. It often involves using a prepared computer (called a ‘Tiger box’) to launch specific types of attacks on the system. It identifies vulnerabilities in a highly controlled environment.
Types of Security Testing Tools
Security testing in software testing relies on various security tools to identify and diminish vulnerabilities. Each type of tool serves a different purpose, allowing for complete protection across various stages of the software lifecycle. Here are the unique features of the main types of security testing tools:
• SAST (Static Application Security Testing): SAST, or static analysis, tools analyze source code or binaries for vulnerabilities without executing the program. This method allows developers to catch issues early in the software development life cycle, such as code weaknesses or likely security flaws that could be exploited. SAST, also known as white box testing, identifies the root cause and fixes it before the application is deployed.
• DAST (Dynamic Application Security Testing): Unlike SAST, DAST tools work by analyzing the application in a running state, and testing for flaws from an external perspective. This approach simulates real-time attacks and focuses on issues that arise only when the application is live, such as misconfigurations or runtime errors.
• IAST (Interactive Application Security Testing): IAST combines elements of both SAST and DAST by monitoring applications as they run and analyzing code execution in real time. This type of security testing in software testing provides more accurate results by observing the application’s behavior during runtime while having access to internal code details.
• SCA (Software Composition Analysis): SCA is a method for analyzing the open-source components and libraries used in applications to identify known vulnerabilities. Many modern applications rely on third-party code, and SCA ensures that these components are up-to-date and secure, helping prevent supply chain risks.
• MAST (Mobile Application Security Testing): MAST tools are designed for testing mobile applications. They evaluate possible vulnerabilities in mobile apps, including issues related to device security, application permissions, and network communication. MAST ensures that mobile apps are protected from unauthorized access of sensitive data.
• RASP (Runtime Application Self-Protection): RASP tools detect and protect against attacks in real-time by monitoring applications during runtime. These tools integrate security directly into the application, allowing them to respond dynamically to suspicious behavior and protect against emerging threats as they occur.
How to Do Software Security Testing
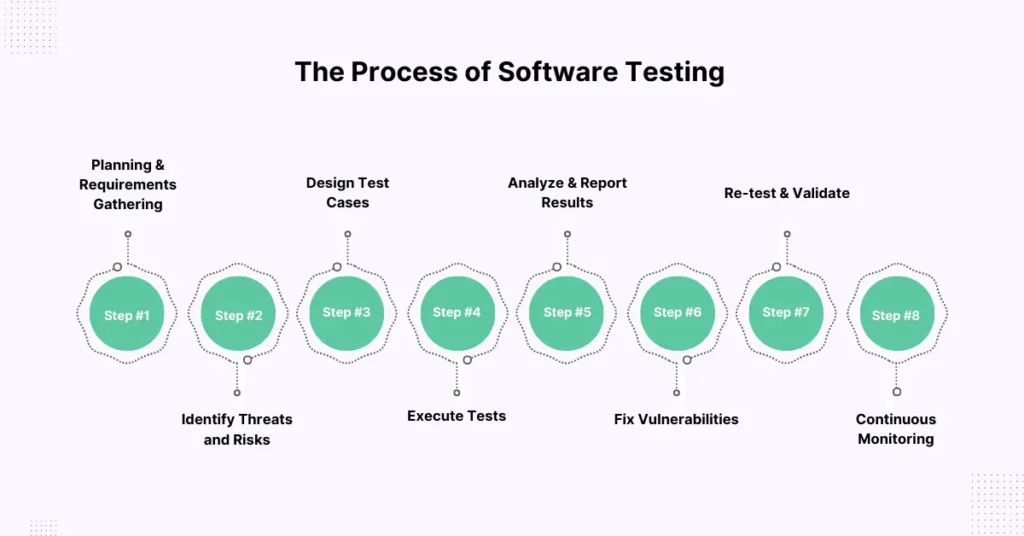 Performing security testing in software testing involves a structured approach to ensure that all potential vulnerabilities are identified and addressed. Here’s a detailed step-by-step process:
Performing security testing in software testing involves a structured approach to ensure that all potential vulnerabilities are identified and addressed. Here’s a detailed step-by-step process:
- Planning and Requirements Gathering: Define the scope of the security testing in software testing. Collect and identify which systems, applications, or components will be tested, what type of testing will be performed (e.g., penetration testing and vulnerability scanning), and what the objectives are. Align the testing goals with the security strategy and specific requirements of the organization.
- Identify Threats and Risks: Next, identify potential security threats and risks. Understand the attack surface, possible threat vectors, and vulnerable areas within the application or system, such as data breaches, denial of service (DoS) attacks, or malware. Tools such as threat modeling can help predict where attacks are most likely to happen.
- Design Test Cases: Based on the identified risks, create test cases to simulate potential attack scenarios. Focus on key areas such as authentication, input validation, session management, and data protection. Each test case should have clear objectives, expected outcomes, and success criteria to ensure the application is functioning as expected.
- Execute Tests: The actual testing begins after the test cases are prepared. Run security tests such as vulnerability scanning, penetration testing, or using tools such as SAST and DAST. Document and categorize all findings, including any vulnerabilities, misconfigurations, or weaknesses that are uncovered.
- Analyze and Report Results: Analyze the results to determine the severity and impact of each vulnerability. Document the findings in a detailed report, prioritizing vulnerabilities based on risk levels and potential impact. This report will serve as a guide for addressing the identified issues.
- Fix Vulnerabilities: Developers and security teams work together to fix the identified vulnerabilities. This could involve patching software, reconfiguring systems, or applying new security controls. Ensure that each vulnerability is properly cleared before moving forward.
- Re-test and Validate: Once fixes are applied, re-test the system to validate that the vulnerabilities have been effectively addressed. Confirm that the security measures are now in place and functioning as intended, ensuring that the system is secure.
- Continuous Monitoring: Security testing in software testing is not a one-time task. Monitor continuously and test regularly to ensure that new vulnerabilities don’t emerge as the system evolves or as new threats develop. Automated tools help in maintaining ongoing security and spotting new risks as they arise.
Common Myths about Security Testing
Security testing in software testing is often surrounded by misconceptions that can lead to ineffective practices. Here are some common myths debunked:
Myth: Security Testing is Only for Large Companies
Reality: Many believe that only large organizations need security testing due to their size and data volume. However, small- and medium-sized businesses are also prime targets for cyberattacks. All organizations, regardless of size, should prioritize security testing in software testing to protect sensitive data and maintain customer trust.
Myth: Security Testing is a One-Time Activity
Reality: Some think that security testing in software development is only needed during the initial phase. In truth, security testing should be an ongoing process. As applications are updated and new threats emerge, continuous testing and monitoring are essential to maintaining security.
Myth: Automated Tools Can Fully Replace Manual Testing
Reality: While automated security testing tools are valuable, they cannot completely replace manual testing. Automated tools may miss complex vulnerabilities that require human intuition and experience to identify. A combination of automated and manual testing provides an extensive security assessment.
Myth: Security Testing is Only About Finding Vulnerabilities
Reality: While finding vulnerabilities is a key goal, security testing in software testing also focuses on understanding the full security posture of an application. It includes validating security controls, ensuring compliance with regulations, and assessing the effectiveness of security measures in place.
Myth: Security Testing is Too Expensive
Reality: Many organizations perceive security testing in software testing as an unnecessary expense. However, the cost of a security breach can be far greater, resulting in financial losses, legal issues, and damage to reputation. Investing in security testing is a proactive step that can save money in the long run by preventing costly security breaches.
Advantages and Limitations of Security Testing
Advantages of Software Security Testing
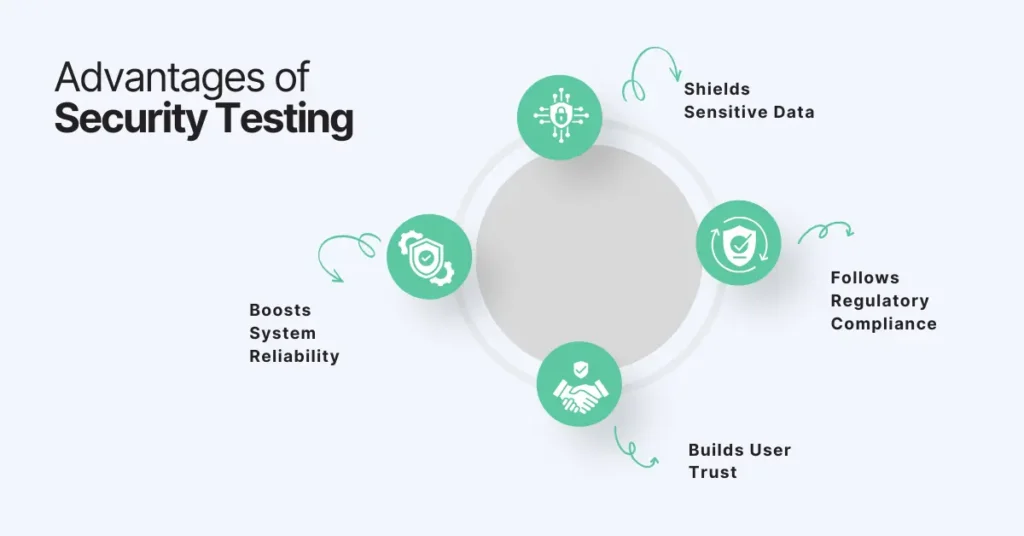 Security testing in software testing provides several critical benefits to both organizations and their users. Below are the key advantages:
Security testing in software testing provides several critical benefits to both organizations and their users. Below are the key advantages:
• Boosts System Reliability: By identifying and fixing vulnerabilities early, security testing in software testing ensures that systems remain stable and reliable. This reduces the risk of unexpected failures due to security breaches or malicious attacks, helping to maintain smooth operations.
• Shields Sensitive Data: One of the primary goals of security testing in software testing is to safeguard sensitive data from unauthorized access. This is crucial for protecting user information, financial data, and other critical business assets, preventing data breaches that could result in severe consequences.
• Follows Regulatory Compliance: Many industries are governed by strict regulations that require businesses to maintain certain security standards. Security testing in software testing helps organizations meet these regulatory requirements, avoiding legal penalties and ensuring conformity with industry standards.
• Builds User Trust: Users are more likely to trust applications and systems that are secure. Security testing in software testing builds confidence by demonstrating that the organization takes proactive steps to protect their data, which enhances user loyalty and reputation in the market.
Limitations of Software Security Testing
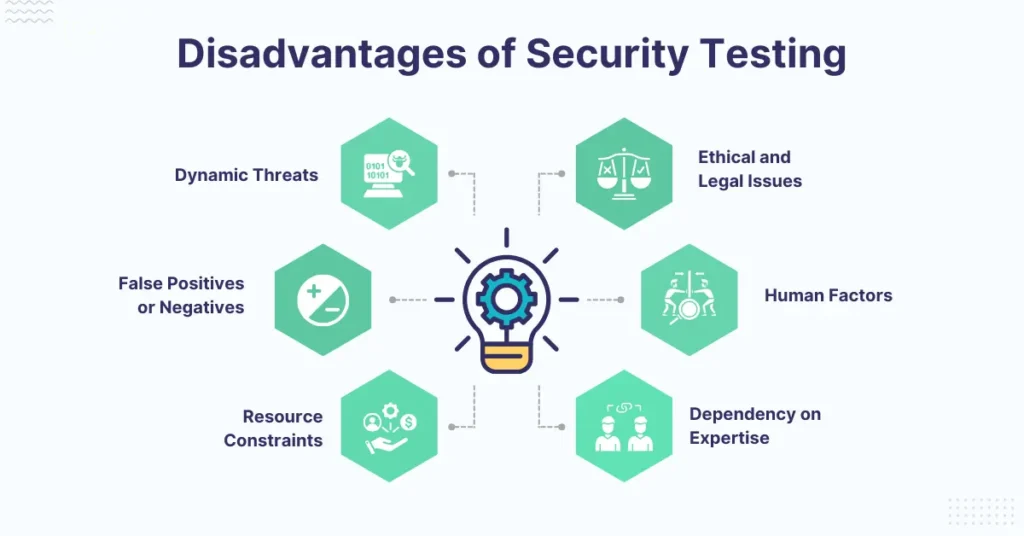 While security testing in software testing is vital for safeguarding systems and applications, it does have some limitations:
While security testing in software testing is vital for safeguarding systems and applications, it does have some limitations:
• Dynamic Threats: Security testing may not identify every possible vulnerability, especially if new threats or zero-day vulnerabilities are not included in the test cases. No security test in software testing can offer 100% coverage against all potential attacks.
• False Positives or Negatives: Security testing tools can sometimes generate false positives (flagging issues that are not real threats) or false negatives (missing actual vulnerabilities). This can lead to wasted resources or confusion.
• Resource Constraints: Security testing in software testing can be resource-intensive, requiring significant time, effort, and computational resources. For smaller organizations, it may be challenging to conduct thorough testing without straining their capacity.
• Dependency on Expertise: Security testing requires specialized knowledge and expertise to perform effectively. Without skilled professionals, it can be difficult to assess vulnerabilities or correctly interpret test results.
• Human factors: Security testing in software testing can be affected by human errors, biases, or assumptions, leading to inaccurate or incomplete test results. It can be influenced by the knowledge, skills, attitudes, and behaviors of the security testers, the data owners, the users, and the attackers.
• Ethical and Legal Issues: Security testing in software testing can involve actions such as exploiting weaknesses, accessing restricted systems, or creating harmful traffic. Testers must follow ethical rules, such as getting permission, respecting limits, minimizing harm, and reporting issues responsibly.
Conclusion
In this blog, we explored the importance of security testing in protecting applications from cyber threats, ensuring system reliability, and safeguarding sensitive data. By identifying vulnerabilities early, organizations can prevent potential breaches, comply with industry regulations, and build trust with their users.
QA Touch offers a comprehensive platform to streamline security testing efforts. With its integrated testing management tools, QA Touch can help you track vulnerabilities, manage test cases, and collaborate with your team more effectively to strengthen your application’s security.
Ready to upgrade your security testing process? Connect with us today to learn how QA Touch can support your testing needs and keep your systems secure.