Penetration testing also referred to Pen Testing or white hat attacks, is an authorised mimic attack on a system and performed to assess the security of the system.
Pen tests can be automated or performed manually. The primary objective of penetration testing is to determine security vulnerabilities of a system or organisation.
Why do we need Penetration testing?
By attempting to break your defences, Penetration testing can help you get a better understanding of your existing security and make improvements to it.
The purpose of Pen Test doesn’t end up testing vulnerabilities, but also identifies the strengths of your system and helps you create a risk assessment for auditing purposes.
“60 percent of small businesses fail within six months of a cybercrime attack” stated by the National Cyber Security Alliance. Pen Testing can help you to prevent costly damages by cyber attacks.
Penetration Testing Phases
The process of penetration testing is simplified into five phases:
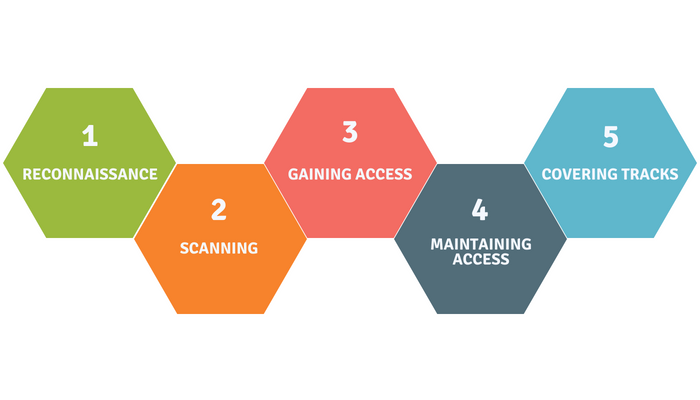
Reconnaissance
The first stage involves gathering relevant information on a target system(how a target system works and its potential vulnerabilities).
This information can be used to define the scope and goals of testing, and the testing methods to be used.
Scanning
The next step is understanding the target application. How it responds to various intrusion. This scanning is done in two ways
- Static analysis
- Dynamic analysis
Gaining Access
Gaining access from the knowledge base collected earlier in reconnaissance and scanning phases helps the tester to intrude the targeted system and uncover target’s vulnerabilities.
This stage uses web application attacks, such as cross-site scripting, SQL injection, and back doors. Then the tester tries to damage the system to understand & measure the damage that a hacker can cause to the system.
Maintaining Access
In this stage, the goal is to persistently stay within the target environment to gather as much data as possible. The purpose of this phase is to simulate advanced persistent threats that stays up in a system undetected for months to steal an organisation’s most sensitive data.
Covering Tracks and Report
This phase is the final phase here the results of the penetration test were compiled into a report including
- Vulnerabilities of the target system.
- Data accessed and damage caused
- Amount of time a hacker could persist in system undetected.
Types of Penetration Testing
The major types of penetration testing include:
- Black Box Testing
- White Box Testing
- Grey Box Testing
Black Box Penetration Testing
In black-box penetration testing, the tester receives no information about the target system apart from the name of an organisation or system.
This test can be done by an internal resource or by an external hacker. It simulates an attack by an external hacker who had cracked the system without any information.
White Box Penetration Testing
In White Box Penetration Testing, the tester receives a wide range of information about the systems including network details, authentication credentials and source code.
It simulates an attack by an internal resource who has access to the organisation’s data.
Grey Box Penetration Testing
In this type of testing, a tester is usually provided with a partial or limited information about the system. It simulates an attack by an external hacker who have gained illegitimate access to an organization’s data.
Free Pen Testing learning resources
- PicoCTF (High school level)
- Veronis (Beginner)
- Tutorialspoint (Beginner)
- PenTest Guru (Intermediate)
- Cybrary (Advanced)
- Webgoat (Intermediate)







